MITRE ATT&CK & Cyber Risk Institute Mapping (06/25/2025)
When I get started on something new, I just keep on going until I get bored with it or have finished as many processes as I can.
When I was going on an API kick, I connected to as many platforms as I had access to.
Now, I have been mapping MITRE ATT&CK with as many security frameworks as I have within my BCWHS application.
First it was mapping with CISA's CVEs.
Then I moved onto mapping to NIST 800-53 and now I have uploaded the Cyber Risk Institute framework (318 controls) and added the mapping for MITRE.
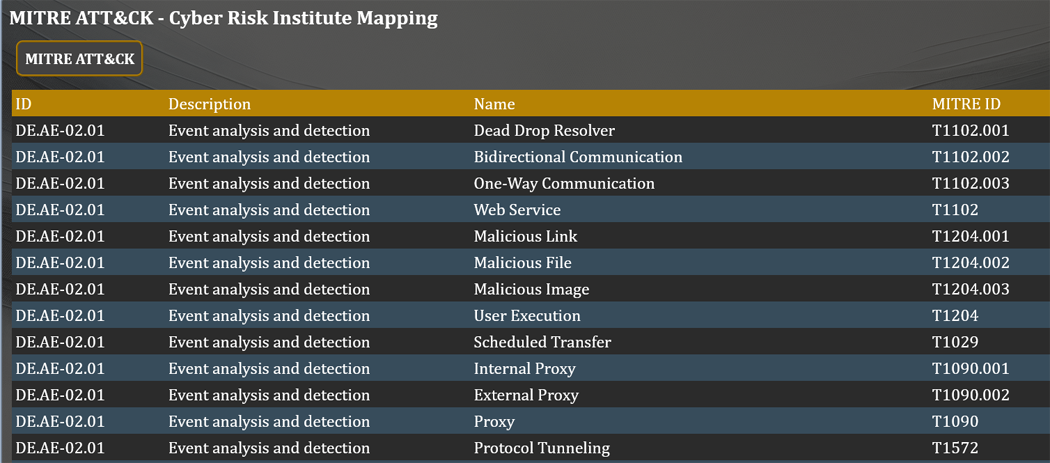
The mapping was fairly straight forward and I managed to knock it out in a few hours.
I am coming to the realization that mapping frameworks to MITRE is a tough one to dig through (easier to program)
as there are controls that map to hundreds of MITRE ATT&CK capability groups which expands the rabbit hole to new levels.
This is why I am a bigger fan of creating your own proprietary framework where you can pick and choose controls that match your organizational risk appetite.
I might plan on mapping Azure and M365 by next weekend...maybe.
BCWHS.com

