Adobe ColdFusion Hackathon (6/18/2025)
I have read a few blog posts from several people who submitted code for the Adobe ColdFusion Hackathon and there is tough competition.
I had limited time due to Father's Day activities and didn't want to take time away from my daughters.
I submitted my code on Friday afternoon and only made it 2/3 through what I wanted to accomplish.
The concept was simple, call out to CISA CVEs JSON file and crunch the data to come up with some cool ways to display charts and the data.
The first phase was to show all CVEs and break them down into pie, line and donut charts.
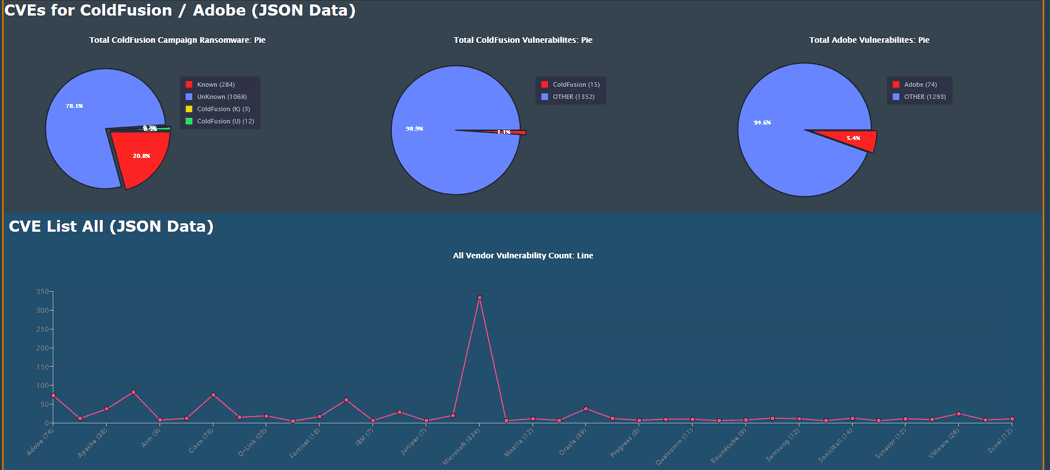
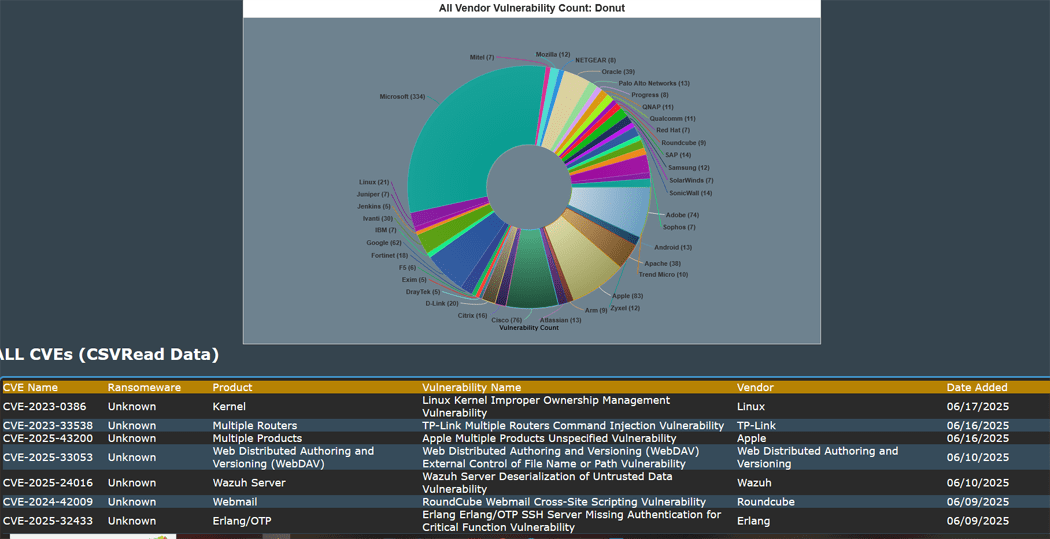
The second phase was to show the data down to the Vendor and display those CVEs in similar but different line and donut charts.
In these 2 phases, I was able to incorporate 9 new features, functions and enhancements.
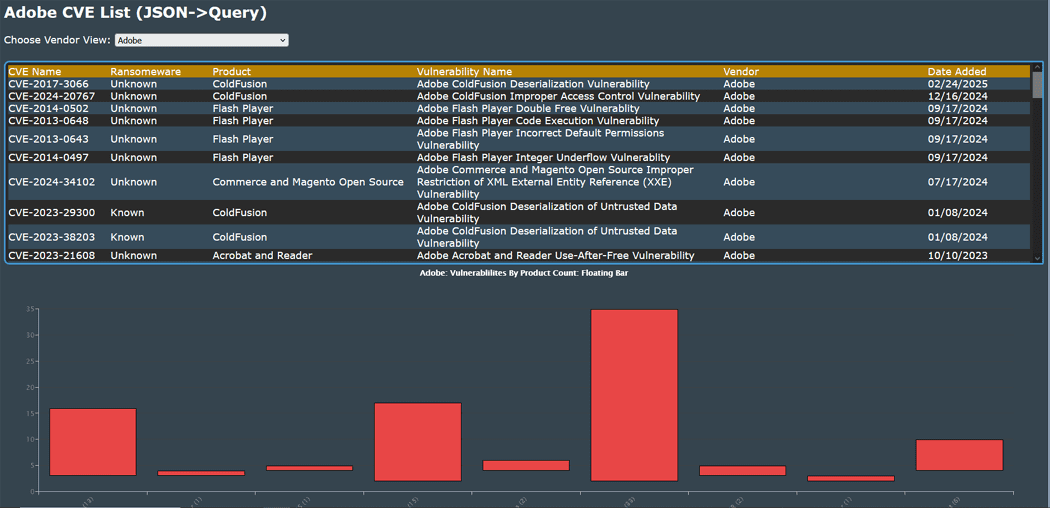
The last phase was to list several selectable products from the CVE list and generate a custom list of CVEs based on a product stack.
I didn't get this part in the contest, but I have created phase 3 in CF 2023 which is what my current hosting has to offer.
I collect CVEs with my own application so I would expand phase 3 and create a new phase 4 which is to create a new G.R.C. plan based on CVEs.
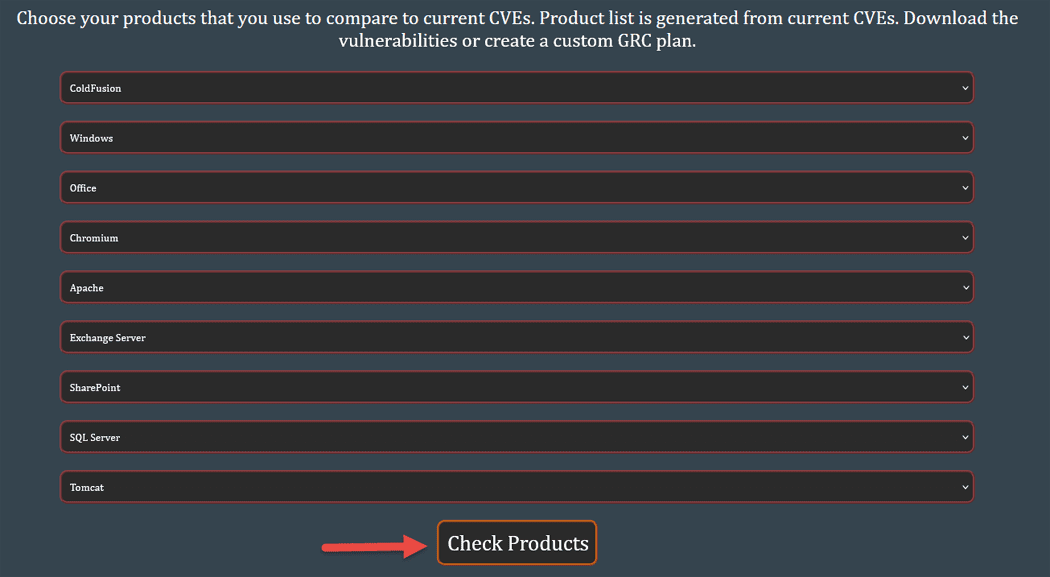
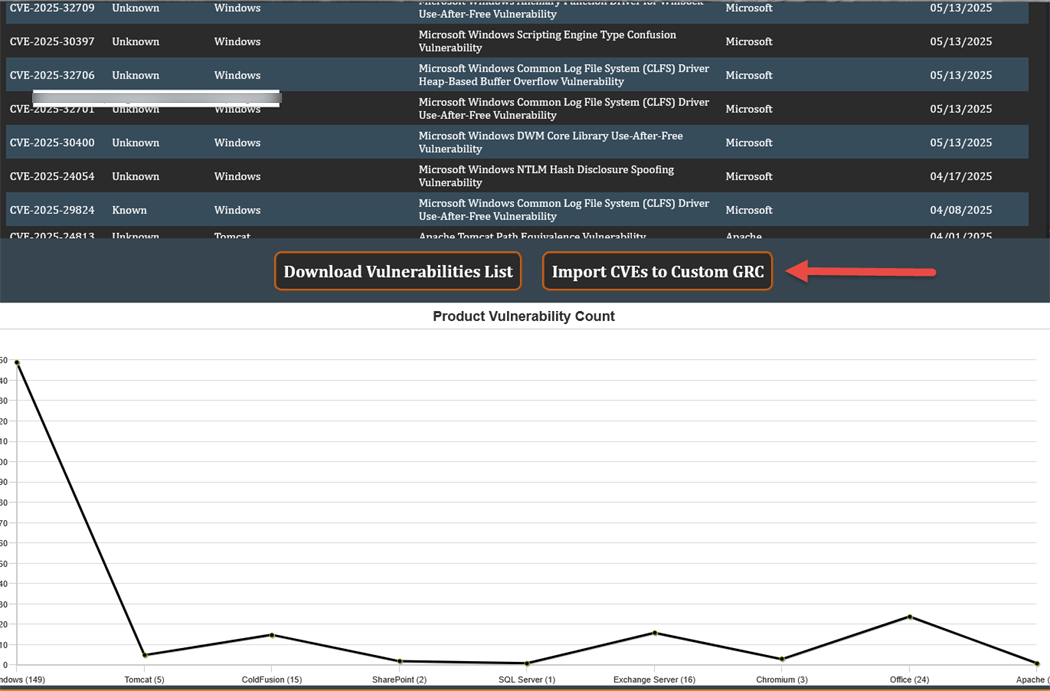
The logged-out version allows you to compare 5 products which displays a list of CVEs and charts.
The logged-in version allows 9 products, a link to download to excel and an import function that creates a custom GRC plan which you can utilize a Risk Register and POA&M and knock out CVEs based on your risk appetite.
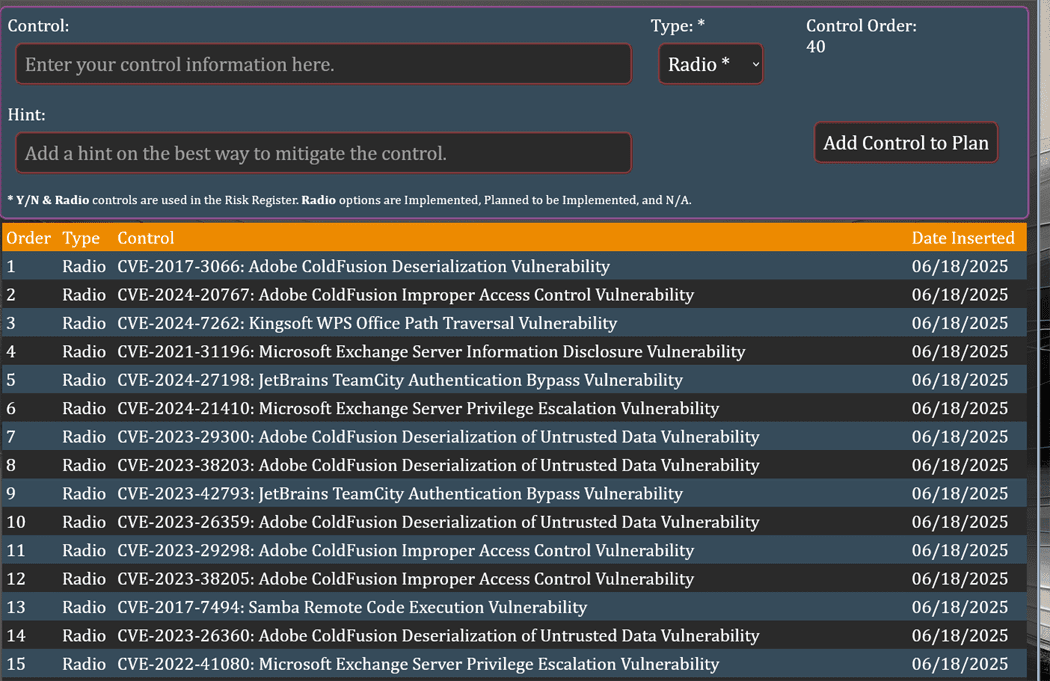
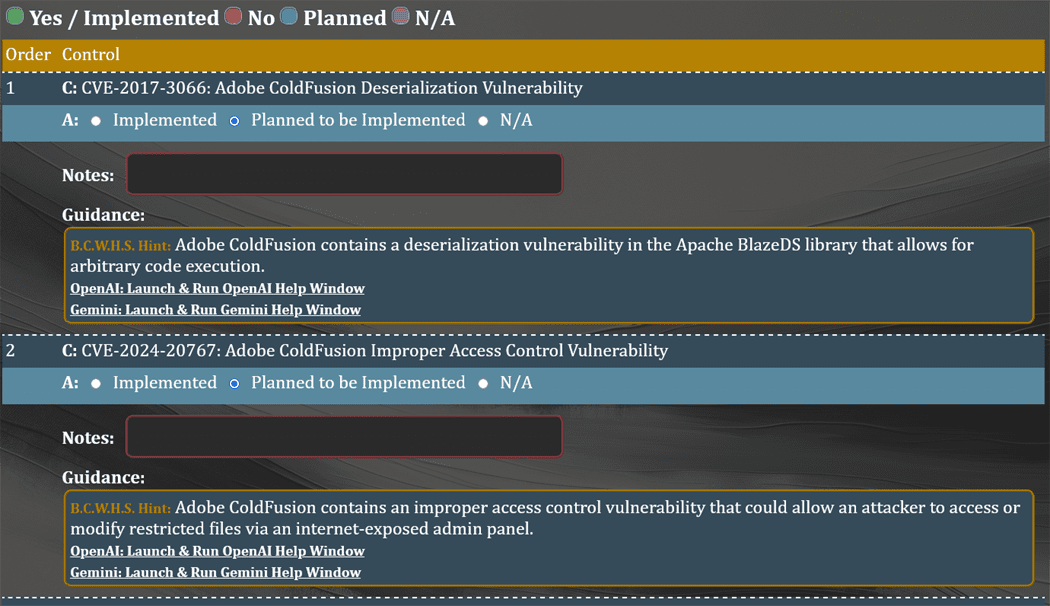
It was a fun hackathon, and I learned new ways to get things done, and found a new way to utilize the CVEs. I doubt I will place due to the known names involved with the contest, but it was fun, nonetheless.
Check it out for yourself.
https://blackcatwhitehatsecurity.com/cveProducts.cfm

